Use LSM to protect both user data and configuration data
|
|
| Linux Kernel core security module is Discretionary Access Control (DAC) and it is directly inherited from Unix. DAC seems to be
outdated for modern security threats and it does not protect against flawed or malicious code. |
|
| To overcome the flaws of DAC, Linux Kernel came up with Linux Security Modules (LSM) Framework that support different security models
such as: |
|
- Smack
- SELinux
- AppArmor
- TOMOYO
- Yama
|
|
 |
|
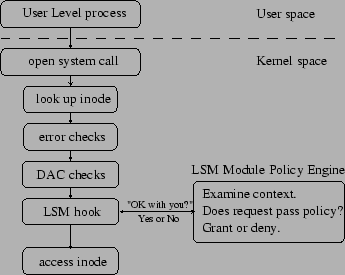
| Source: se7so.blogspot.in/2012/04/linux-security-modules-framework-lsm.html |
|
|
| The Linux Security Modules (LSM) subsystem has developed a lightweight, general purpose, access control framework for the Linux kernel
that enables many different access control models to be implemented as loadable kernel modules. |
|
Smack
|
|
| The Smack LSM was designed to provide a simple form of MAC (Mandatory access control) security . |
|
| Smack includes three important components as follows: |
|
- A kernel module that is implemented as Linux security module.It works best with file systems that support extended attributes.
- A startup script that ensures the device files have correct Smack attributes and load the smack configuration
- User space tools like smackload, smackaccess and chsmack.
|
|
| Implementing Smack includes below steps |
|
- Building Linux kernel image with Smack (i.e..CONFIG_SECURITY_SMACK) enabled.
- Mounting the smackfs filesystem.
- Assigning subject and object label for respective files.
- Creating and updating the rule to Smackfs filesystem.
- Switching to non-root user mode and test the rule.
|
|
Secured Images Running in eSOM's
|
|
| We tested all the above techniques in e-con SOM's. |
|
| Let us show you an example |
|
Module Signing
|
|
| To confirm whether a module is signed, enter the command modinfo followed by module name |
|
|
|
|
| Module signing will restrict loading unsigned modules |
|
|
|
|
| And it won't load modules signed with invalid key |
|
|
|
|
| It will allow loading only valid signed modules |
|
|
|
|
LoadPin
|
|
| When loadpin is enabled in the kernel , it will mark the filesystem device that load the first module when kernel is booted. |
|
|
|
|
| And if you try to load a module inside that specific filesystem (dev(179,34)) from any path , modules will be loaded successfully. |
|
| But if you try to load the module from some other filesystem , the LoadPin will not allow the module to load. |
|
|
|
|
ELF Signing
|
|
| If you execute the signed binary, then it will run successfully |
| |
| root@esomimx6s:~# ./hello_world.sign |
| Hello World |
|
|
| Now again sign the hello_world application with duplicate private key and try to execute the binary, it will be killed by kernel ELF handler. |
| |
| root@esomimx6s:~# openssl genrsa -out duplicate_priv_key 1024 |
| root@esomimx6s:~# ./signelf -i hello_world -o hello_world.sign -p duplicate_priv_key -c signing_key.x509 |
| root@esomimx6s:~# ./hello_world.sign |
| [ 15.104452] ELF Signed with invalid key |
| Killed |
|
|
|
|
Smack
|
|
| We validated Smack LSM Module on our eSOM devices. |
| |
| Created a user named econ and an executable file "read" to read the contents of "myfile" text file. |
| |
| Created subject label for "read" executable file and object label for "myfile" text file.Wriitten a ruleset for subject read on object myfile with
write permission alone and updated the ruleset to Smackfs filesystem. |
| |
| Switched to non-root user and then validated the rule. |
| |
| root@esomimx6q:~# su - econ |
| esomimx6q:~$ ./read |
| File Not Opened |
|
|
|
Conclusion
|
|
| You can secure all your embedded Linux systems with software security approaches explained above. |
| |
| Other way to enhance your system security to next level is by utilizing your processor hardware capabilities like CAAM and HAB present in
iMX6. |
| |
|
|