Key Takeaways
- Why Secure Boot is the first checkpoint in embedded boot cycles
- Importance of implementation on Jetson Orin NX and Orin Nano modules
- Why Secure Boot matters in Edge AI
- How Secure Boot strengthens AI vision box deployments
Edge AI systems handle data and inference tasks directly on embedded devices. When deployed in the field, any unauthorized firmware or modified kernel can compromise results, expose sensitive models, or even damage connected sensors. Secure Boot prevents these compromises at the most critical moment, which happens to be the first power-on.
It verifies every executable block in the startup chain. That way, Secure Boot ensures that only trusted firmware and operating system components run on the Edge AI vision solutions powered by NVIDIA Jetson Orin NX and Orin Nano modules.
In this blog, you’ll learn about Secure Boot, how it works at the hardware level, and its advantages for vision deployments such as e-con Systems’ Edge AI Vision Box.
Secure Boot: The First Checkpoint in Boot Cycles
Secure Boot builds a cryptographic chain of trust starting from the silicon itself. Each stage validates the integrity of the next before execution. On Jetson platforms, the sequence begins with the BootROM embedded in the chip.
- The BootROM contains immutable code burned into the SoC. It authenticates the Bootloader (MB1) using NVIDIA’s public key.
- Once verified, MB1 loads the MB2 stage and transfers control, continuing the validation process.
- The next layer, UEFI firmware, checks the kernel and other boot-critical binaries through signed certificates and public key infrastructure (PKI).
- If a single component fails verification, the boot halts immediately, blocking any unverified or malicious code.
Secure Boot Explained in Orin NX/Nano Modules
In NVIDIA’s Jetson Orin NX and Orin Nano, Secure Boot is integrated into the Unified Extensible Firmware Interface (UEFI). When activated, it validates every binary that loads during startup. The process uses hardware fuses to store public key hashes, ensuring that only code signed with the corresponding private key can execute.
The framework below creates a consistent chain of validation from power-on to OS launch, ensuring the Edge AI vision firmware always runs in a verified state.
- Key hierarchy
The platform supports a hierarchy of Platform Key (PK), Key Exchange Key (KEK), and signature databases (db, dbx). These establish trust between firmware, OS, and drivers. -
Fuse configuration
Once the production fuses are burned, the device cannot boot unsigned code, making it tamper-resistant even at a hardware level. -
UEFI enforcement
Each component, from UEFI drivers to kernel images, is checked through digital signature validation. Any unauthorized change leads to immediate rejection.
Why Secure Boot Matters in Edge AI Deployment
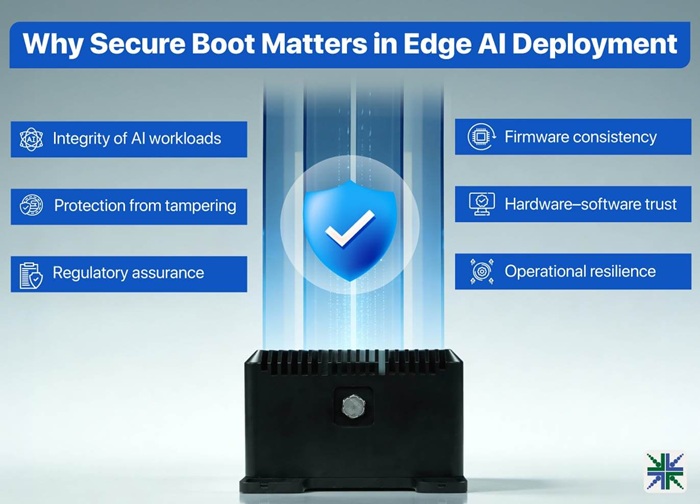
- Integrity of AI workloads: Prevents unauthorized binaries or AI models from running on the device.
- Protection from tampering: Stops root-level manipulation that can corrupt inference data or compromise connectivity.
- Regulatory assurance: Simplifies compliance for industries that demand verifiable startup security, including healthcare, transport, and automation.
- Firmware consistency: Maintains version integrity during over-the-air updates, preventing rollback to vulnerable firmware or use of unsigned images.
- Hardware–software trust: Synchronizes authentication between the module’s silicon fuses and UEFI firmware, creating a unified trust path from chip to application.
- Operational resilience: Preserves stable startup behavior even if devices face power loss, data corruption, or exposure to compromised peripherals.
How e-con Systems Strengthens Security in the Edge AI Vision Box Deployments
e-con Systems has been designing, developing, and manufacturing OEM camera solutions since 2003. Building on this expertise, we develop secure Edge AI Vision Box-Darsi for industries including Mobility, ITS, retail, and industrial automation.
Our proven track record in designing every component of the edge AI vision box makes the entire journey more seamless, from camera module selection to quick integration of drivers and image processing systems. We also incorporate Secure Boot as part of its system validation pipeline for the Edge AI Vision Box.
Our key strengths:
- Elite partner of NVIDIA – with deep engineering expertise and access to NVIDIA’s tools and platforms.
- A growing network of sensor manufacturers like onsemi, Sony, and OmniVision
- Strong technical expertise in optics integration, utilizing machine-aligned fine focusing and gluing methods
Learn more about e-con Systems’ Edge AI Vision Box.
Browse our Camera Selector Page to explore form factors and interface options for your edge AI vision applications.
To discuss your specific vision requirements, please get in touch with our team at camerasolutions@e-consystems.com.
FAQs
1. How does Secure Boot protect the Edge AI vision during startup?
Secure Boot checks digital signatures at every boot stage, from BootROM to the operating system. Only firmware and software verified with NVIDIA’s trusted keys can load, blocking any altered or unauthorized binaries before they execute.
2. What happens if a component fails Secure Boot verification?
If any file in the boot chain lacks a valid signature, the system halts immediately. This prevents tampered firmware, kernel, or OS layers from running, protecting AI workloads and connected sensors from compromised code.
3. Does Secure Boot affect system performance or boot time?
Secure Boot on NVIDIA Orin platforms leverages the on-chip Security Engine to perform hardware-accelerated authentication and decryption. The process adds negligible latency while offering continuous integrity verification, making it ideal for performance-driven Edge AI systems.
4. Can users update software after Secure Boot is enabled?
Yes. Firmware or OS updates can be applied as long as they are properly signed with the authorized private key. Secure Boot validates the new signature to confirm authenticity before accepting the update.
5. Why does Secure Boot matter for Edge AI deployments?
Edge AI systems often operate outside secure data centers. Secure Boot ensures that the vision deployments always start in a trusted state, guarding against firmware tampering, version rollback, or unverified software in the field.

Prabu is the Chief Technology Officer and Head of Camera Products at e-con Systems, and comes with a rich experience of more than 15 years in the embedded vision space. He brings to the table a deep knowledge in USB cameras, embedded vision cameras, vision algorithms and FPGAs. He has built 50+ camera solutions spanning various domains such as medical, industrial, agriculture, retail, biometrics, and more. He also comes with expertise in device driver development and BSP development. Currently, Prabu’s focus is to build smart camera solutions that power new age AI based applications.




